Camera technology has evolved over the last couple of decades to the point where consumer-grade cameras are decent quality, but fairly inexpensive, and therefore cameras have become fairly pervasive. In general, having a camera is a good thing – it is a way to increase your awareness, and if the camera is being recorded, the camera can be a witness on your behalf. However, in certain situations, having a camera can work against you as well. We will explore several scenarios where your privacy and / or rights could be compromised, as well as technology recommendations for protecting them.
Table of Contents
Introduction
Inexpensive, yet powerful cameras have become a part of everyday life. Owning a camera system can be a great benefit – it allows you to be more aware of what happens when you’re not physically present.
- A camera can be a silent witness, allowing you to identify porch pirates, and document other types of crime in order to assist law enforcement.
- A camera can deter crime – if a potential criminal can see a camera, or you post warning signs, someone is much less likely to commit a crime on your property, knowing that their face or license plate might be recorded.
However, cameras record ALL activity, not just the activity you want recorded. You can quickly find yourself in a situation where your camera is now “evidence” against you.
Types of Cameras
There are many different types of cameras.
Doorbell Cam
Systems like the Ring Doorbell have revolutionized the simplicity and functionality of security cameras. With motion sensing capability, as well as two-way communication via a smart phone, and cloud video storage, a doorbell cam is a quick and easy way to upgrade your home security.
Doorbell cams are a great way to catch porch pirates, but also provide excellent protection for the front of your house.
With two-way voice communication, you can “answer” the door without opening it. If someone has ill intentions, you can instantly inform them that they are being recorded, the police are on their way, and you ain’t openin’ the door no matter what they say.
Doorbell Cams are often cited as the “killer application” for security cameras.
Dashboard Cameras
Dashboard (“dash”) cams continuously record as you drive. Some are more sophisticated than others, with features such as:
- Front and Rear recording
- Side recording
- Collision sensing (G-sensor)
- Acceleration / deceleration events
- Pre-event Recording (record a few minutes before an event occurs)
- GPS location + velocity / altitude tracking
- “Parking mode” passive surveillance using motion detection
- Integration with OBD vehicle diagnostics bus to snapshot vehicle speed, engine RPM, and the position of various driver controls
In “the age of entitlement”, people avoid personal responsibility, by lying and shifting blame. Meanwhile, some unsympathetic and incompetent insurance companies refuse to accept liability for their entitled clients. And you are basically on your own. Having a dash cam can be your witness, and ultimately, your salvation from legal or financial liability.
Outdoor Surveillance Cameras
Like doorbell cams, outdoor surveillance cams can catch porch pirates as well as any other activity on your property. Outdoor cameras have night vision capability, and might record to the cloud via WiFi or to a central DVR.
Indoor Surveillance Cameras
The inside of your house is a sensitive place. By law, your home is your castle, and what happens in your home is the most protected area, by law. But more than that, the inside of your house is a place where you are supposed to be safe and secure from the outside world.
However, even inside your house, there are situations where you want the ability to see what’s going on, or a record of what occurred.
Most indoor cameras have the ability to set recording times, for example, to only record when you are asleep or not at home, and to configure “masking” which prevents recording a specific portion within the camera’s field of view. Masking is useful to prevent recording sensitive areas, for example, inside a bedroom if the door is left open, yet the camera can otherwise freely record what happens outside the bedroom.
Game Cameras
If you own property or a lease, you want to track the game. You can put out a feeder, and a motion-activated game camera so that you can track what animals are eating the food. Game cameras have some basic features in common:
- Run on batteries
- Strap or affix to a tree or deer stand
- Wide field of view
- Motion-activated
- Stores pictures and video to a memory card
Higher-end cameras have a built-in WiFi or data connection, and can be accessed remotely from a cell phone.
Hidden Cameras / Nanny Cams
“Nanny Cams”, popular in the early 2000’s, are cameras built in to an otherwise innocuous devices such as alarm clocks, radios, or smoke detectors, allowing parents to monitor their child’s care by a nanny or babysitter. Nanny cams quickly became a popular way to monitor anyone who provides a service in your home, especially if you aren’t there at the time. For example, a nanny cam is a great way to prove or disprove whether the house cleaner is stealing, or if your plumber is ripping you off.
However, these have dropped in popularity with the advent of tiny, inexpensive, WiFi-enabled cameras that are the size of a coin, that can literally be hidden anywhere.
Other Camera Features
All cameras store pictures and / or images on a memory card, to the cloud, or on a centralized DVR.
Some have these additional features:
- Allow you to access pictures and video from a phone, either remotely via WiFi, from the DVR via WiFi, or via the cloud.
- Record Audio and / or allow two-way audio communication
- Audible alarm
- Participate in a WiFi mesh network
- Configure recording times and / or masking
- “Pre-event” recording, which records a minute or two prior to a motion event
- Tie-in for a security system with the ability to trigger an alarm or be triggered externally by an alarm
- Most cameras have passive night vision capability, but some have infrared illuminators (active night vision) as well. Typically, these can be set to turn on and off automatically or at preset times.
DVR Features
If tied in to a DVR (Digital Video Recorder), the DVR typically has these features:
- View multiple cameras
- Picture / video storage for several weeks
- Limited video editing
- Download to USB
- Tie in to cloud storage
- View remotely via WiFi or cloud
Risks of Having a Camera System
As discussed, a camera system can be an excellent tool:
- A camera can be a witness to a crime or capture a situation where liability is involved, such as a car accident.
- A camera can allow you to remotely monitor your house, car, or property, so that you can react quickly to a problem.
- Cameras can help you ensure that your children and pets are properly cared for, and properly behaving.
- Cameras can help you ensure that services you pay for, are properly provided.
- Cameras can help you monitor your property for wildlife, pests, and trespassers.
However, having a camera can also put you at risk if they aren’t configured and managed properly.
Your Camera Can Be A Witness Against You
We should all try to be good, moral people who handle their problems like adults, which includes owning up to mistakes. But, having those mistakes caught on camera might cause you problems or cast you in a bad light.
- If you get in to a car accident, having a dash cam could prove that the other driver was at fault. However, if you caused the accident, or acted recklessly, it would show that as well.
- If someone steals your packages or your lawn ornaments, having a camera can help identify the suspect. However, if you bump in to your neighbor’s car, or back in to his trash cans, your camera will record that, too.
- Your home is your castle, and if someone inside your home is committing a crime or doing something wrong, a camera is a great way to catch them. However, if YOU commit a crime or act inappropriately inside your house, your camera will record that, too. Maybe you smoke a joint in a state where it’s not legal, or, maybe your girlfriend visits while your wife is out of town. Maybe your kid breaks in to your liquor cabinet and serves alcohol to his underage friends. Hopefully, you and your family don’t engage in these types of activities, but all of this could be caught on camera and could land you in hot water.
- You could inadvertently commit a crime that gets recorded on camera. There are so many laws that can overlap and become convoluted, that you might be breaking a law and not even know it. For example, if you are under the age of 21, you are not allowed to possess handguns and alcohol. If you give your kid a handgun for Christmas or give him a sip of your beer, you could be breaking the law. Those are obvious situations but there are many that aren’t. For example, if you park in front of your own house, facing against traffic, this might be breaking a local ordinance. And if your camera is pointed at your car, you’ve just recorded yourself committing a civil infraction.
Your Camera Can Be A Tool for Law Enforcement
If someone breaks in to your house, hits your car, or steals your stuff, the first thing you’re going to do is download your camera recording and hand it to the cops. THE GOOD GUYS WIN.
However, let’s say that a crime occurs in the street in front of your house, or across the street on the neighbor’s property. The first thing the cop is going to do is look around, see your cameras, and ask to see the relevant recording.
There are several scenarios that could play out at this point.
- Being helpful, you invite the cop in to your house, allow him to review the recording, and download a copy on to a memory stick for him. Unfortunately for you, if the cop sees something suspicious, such as something he BELIEVES is drug paraphernalia or bomb parts inside your house, he can use that as reasonable articulable suspicion to obtain a search warrant, and now he can search your entire house for drugs or bombs. Cops ARE NOT experts. So maybe what he thought was drugs or a bomb was really your kid’s science experiment. But at this point, simply HAVING a camera put you under the scrutiny of the police.
- Same situation, but while reviewing the recording of the front of your property, he also sees a recording of your cousin Frank ripping a bong in your living room while you weren’t at home. Same result – search warrant.
- Let’s say that instead of being helpful, you tell the cop to fuck off. He can get a search warrant to seize your DVR, and any other recording devices, perhaps and including the cameras themselves. And, because the DVR is evidence, the cops don’t have to give it back. And, as above, AFTER they have searched your entire house, they might find “evidence of a crime” while reviewing the video, and search your house AGAIN. Or, arrest you.
- Let’s say that it’s a doorbell camera, and you don’t even have a DVR. This time, you try to be cooperative, and you send the cop a link to the video clip. However, maybe the cop sees something suspicious in the video. Now he can get a warrant to have your doorbell company provide ALL of your doorbell recordings. If he observes the crime he suspected you of, or even if he observes you committing a completely different crime, he now has all of the evidence he needs. He can literally give you a ticket at that point (or worse), for a civil infraction (or a crime) based on video that YOU provided to him.
- Let’s reverse (again), and you tell the cop to fuck off (again). When you created an account and signed up with your doorbell service, you signed an agreement which allows them to comply with law enforcement demands. In many cases, these companies don’t even require a warrant… they just hand over whatever the cops request. Even if they do require a warrant, the cop can get one based on the REASONABLE suspicion that the camera captured the original crime. And, maybe you have a couple of internal cameras linked to the same account…well, he now has access to recordings from inside your house, as well.
- Let’s consider a scenario where there was no preceding incident at all, but the cop directly suspects YOU of being a criminal. By simply observing that you have a doorbell camera, he can get a warrant for your doorbell camera, as well as any other cameras tied to your account, which might include internal cameras. Typically, the doorbell companies will hand over these recordings without informing you, and in fact, they may be prevented by law enforcement from informing you. Now, without your knowledge or consent, the cops could have video recordings from inside your house.
Your camera could catch a criminal, or turn you in to one.
Cameras Can Leak Private and Sensitive Information
One of the many innovations brought to the auto market by Tesla is their always-on cameras that are part of the car’s security system. During the post-election madness of 2024, many people were caught keying Tesla vehicles, and the way they were caught is that they were recorded by the car itself.
However, in 2023, Tesla employees were caught sharing sensitive images that had been recorded from peoples’ cars that were parked inside a garage or had a field of view that included sensitive areas.
With Tesla leading the way, other car manufacturers are now including similar always-on cameras, but it’s up to each individual car company to determine how that data is stored and processed. In some cases, you may be granting your car company rights to sell video and audio recorded by your car under a wide variety of circumstances. to third parties who mine this data and use it for purposes outside of your control. One trick that these companies are using is to have the salesperson click past the click-and-accept prompt on your behalf, where these terms would normally be explained in detail. Once “activated”, the system now silently runs in the background recording and sharing your audio and video.
But, it’s no longer just cars. As cameras become a prevalent feature on other smart devices, the risk of leaking sensitive information increases accordingly.
Beyond leaking “sensitive moments”, these cars and smart devices could be leaking anything within the camera’s field of view, which is then combined with GPS other geolocation data, sold, and ruthlessly mined by data brokers:
- Your image, your spouse’s image, and images of your children
- Your age, weight, height, skin color
- Your religion, politics, and sexual orientation
- Not only where you shop, but what types of products and brands that you purchase
- Disabilities and health information
And the list goes on and on. In fact, Nissan was called out by Mozilla as the worst offender for collecting sexual activity, health diagnoses, and genetic data. Although car and smart device companies collect way more than just your camera footage, the ability to literally see what you are doing when you are in or near your car or other smart device takes this egregious practice to the next level.
Cameras Are Hacker Bait
Like most “Internet of Things” (IoT) devices, WiFi-connected cameras and DVRs might have impressive hardware, but often, the firmware (device software), website, and smartphone app are a mess of crappy coding and open source components that were cobbled together just enough to make the product work, but not known for being hardened and secure.
This makes IoT in general, but specifically camera systems, a desired target for hackers. Once a hacker has compromised the device, they may be able to do much more:
- Compromise your online account
- Download your video files, for example, to use for extortion
- Use your devices against you, for example, enabling an indoor camera without your knowledge
- Use the device as an attack vector to compromise your internal network. Once a hacker is inside your network, they could steal more data, compromise other online accounts, or compromise other systems.
Unfortunately, many IoT vendors, including Camera and DVR manufacturers, are slow to release security updates, which means that these devices could be sitting inside your network with a known vulnerability that can be exploited by a moderately-trained attacker.
Technical Recommendations – How to Protect Yourself
Limit The Use of Cloud Storage
Cloud storage has the advantage that if your house is burned or burglarized, your video evidence is stored safely “in the cloud”. However, you want to make sure that your provider offers robust encryption:
- First and foremost, your provider should encrypt your files in transit and at rest.
- Typically, files would be uploaded using TLS – the same protocol that allows you to do your banking and amazon shopping online safely. This prevents someone from intercepting the file as it is being transmitted.
- Once stored on the “cloud” server as files, the recordings should be stored ONLY in an encrypted state. This prevents them from being stolen if your provider is hacked. Storage encryption may be a feature that you have to enable or opt-in to, so be sure to check.
- Ideally, your provider should offer “tenant encryption keys”, where each customer receives their own encryption key, which prevents anyone else, including the provider, from viewing the files. Ring calls this “E2EE” or “End-to-End Encryption”. If your provider offers this or a similar feature, it may be something you must enable or opt-in to, so be sure to check.
Likewise, ONLY store what you need. It seems like a good idea to store 30+ days of recordings, because, hey you might need them, right? In fact, the more data you store in the cloud, is more data that can be hacked, stolen, or seized by law enforcement.
- Set your cloud storage history to 1 day (24 hours) or 2 at most
- If you have video evidence that you need to preserve, download it! Once the video is in a format that you can use (off of the cloud provider’s servers), you can still share it with your friends, neighbors, or law enforcement by using Google Drive.
- As long as the video is not considered to be evidence, and doesn’t contain anything sensitive, consider posting it on a video sharing website.
NEVER Use Biometrics
| Note: NEVER use Biometric authentication. The police can get a warrant to forcibly use your fingerprint or your face to unlock your phone. The best defense is to use a conventional password or unlock pattern that can’t easily be guessed. Even if a judge issues a warrant or a subpoena to try to compel you to unlock your phone with a pin, pattern, or password, this falls under the 4th amendment, but somehow, biometrics do not because they are “in plain sight”. Even if you are compelled by a judge to unlock your phone using a pin, password, or pattern, you can enter a duress code (if your device supports it) or simply get the password wrong until the device erases itself.
Similarly, even under duress, you can’t be compelled by a criminal to unlock your phone, as long as you don’t use biometric authentication. |
ALWAYS Use Encryption
Even if you have a DVR and don’t use cloud storage, USE ENCRYPTION.
- Make sure your DVR supports AES encryption.
- If not, use an external, encrypted drive. Although not inexpensive, USB drives with an external pin pad are quite common.
- If your DVR runs on Linux, be sure to encrypt the storage volume
- If you download videos to your phone, use an encrypted folder
Some things to consider:
- Ideally, you want the encryption key to be something you enter every time the system boots. However, this also means that if the system is disrupted, it will stop recording.
- If the drive and the encryption key are stored together, this defeats the purpose of encryption. So the key must be external and removable.
- You want to run your entire camera system on a UPS (Uninterruptible Power Supply) so that it keeps recording even if the power fails
- Be sure that your encryption scheme is based on commercially-available (including open-source) software, so that you can manually recover the data if your DVR system fails.
Isolate Your Internal Network
Normally, you router connects directly to your broadband via some sort of transceiver installed in your house by your provider.
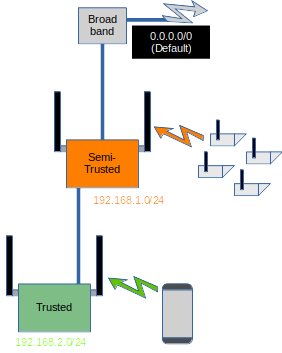
By installing a second router between your normal router and your broadband device, you create a semi-trusted zone, where your cameras can connect without having access to your internal network, because your normal router acts as a firewall. Meanwhile, your trusted devices can access anything, including the cameras. This type of network architecture is known as a “DMZ” – an isolated network segment between the (untrusted) internet and your internal firewall.
Actually, all IoT devices should go in to the DMZ, not just your cameras. This severely limits risk if one of them were to become compromised, because your trusted devices are safely protected behind the second firewall.
Don’t Use Internal Cameras
For all of the reasons discussed above, you just simply should not have a camera inside your house.
| When I bought my alarm system, it came with a “free” internal WiFi camera. The alarm company tried very hard to convince me that this was a requirement for “enhanced” monitoring, so that if an alarm goes off, they can “check on things”. So let me get this straight…you want me to put a camera INSIDE my house that can be REMOTELY activated by YOU when “you suspect” something might be going on. HARD PASS. |
If you absolutely must have an internal camera, for example, to remotely monitor pets or children, make sure it has a physical switch that can deactivate the camera, either via it’s power source or its data connection. It’s not that difficult to wire a switch in to the power cable, or to plug it in to a switched power supply. Get in the habit of turning off the camera when you are at home, and turning it on when you leave.
Depending on the software for privacy and security, in my opinion, is completely inadequate. A camera that is physically-disabled can’t be hacked, manipulated, or coerced.
Adjust the Fields of View
Make sure you adjust the field of view of every camera.
- Although I don’t recommend internal cameras, if you have to have one, make sure it is pointed away from sensitive areas such as bedrooms and bathrooms.
- External cameras should be carefully aimed so that they don’t capture a view inside your own house, nor inside your neighbors’ houses.
- Use software masking, where appropriate.
- Avoid pointing cameras directly toward light sources such as the rising or setting sun
Be Aware of Car Cams / Dash Cams
If you use a Dash Cam or if your car has built-in cameras, be sure you know how to enable and disable them.
Also, make sure that when you park at home, you park in such a way that your car can’t record sensitive video or audio.
If you are in an accident, even if it was your fault, keep recording. Hopefully, we can all behave in a civil matter and let the insurance companies handle it, but you never know when some nut job is going to become enraged and do something stupid. If you have a dash cam, let the camera continue to record during the entire encounter, as an incentive to keep things civil, and a way to provide evidence to the cops if not. Once the encounter is complete, swap memory cards to preserve the evidence. This implies that you should ALWAYS carry a spare memory card for your dash cam.
The Ideal System Doesn’t Exist
But, here is how I would design it.
- The entire system should run from redundant power. This might mean having a central UPS (Uninterruptible Power Supply) that feeds the DVR and all cameras, or multiple UPSs.
- The system should have a local DVR and cameras that connect via WiFi. Ideally, the DVR has a WiFi router built in to it.
- The WiFi should be dedicated to the cameras and DVR, with no other devices using the same network, and WiFi should be configured to only allow a list of known MAC addresses.
- Most cameras, even if they have local storage, allow a “live feed” using JPEG, MJPEG, or MPEG stream compression. A DVR uses the camera’s live feed to record images and live video. Unfortunately, these are much older standards that don’t efficiently compress the data stream. This takes up network bandwidth, but also CPU and memory capacity on the DVR, which must then transcode the feed in to a modern format before it’s stored on disk. Ideally, both the cameras and the DVR should support H.263 / H.264 within a MP4 wrapper. This allows the DVR to stream straight to disk, or display live video, or both, very efficiently, allowing one DVR to support multiple cameras on minimal hardware.
- Traditionally, the DVR connects to each camera in order to access a live feed, and this is what the DVR stores on disk. However, a better scheme is to have each camera connect to the DVR, and push the stream directly to the DVR.
- Each camera should have 24 hours of local storage (ideally, encrypted), where it stores video in the event that the DVR is offline. As soon as the camera is able to reconnect, it should resume the live feed, but also, begin transmitting the locally-stored files to “catch up” to current.
- All camera and DVR files should be stored in open (vs. proprietary) formats. If a camera or the DVR dies, you should be able to mount the memory card or hard drive on a Linux or Windows machine, and be able to immediately view the files without having to transcode them.
- When connecting to the DVR, the camera and DVR should use TLS for encryption, and mutual TLS for authentication. This protects data in transit, and helps prevent Man-In-The-Middle (MITM) attacks.
- All cameras and the DVR should have volume-level AES-256 encryption enabled by default, with a user-configurable encryption key. Using a Key-Encrypting-Key (KEK) scheme prevents hassles with key rotation. Using Open Source encryption tools such as VeraCrypt allows cross-platform access to encrypted volumes in the event of a hardware failure.
- The cameras should be configured to auto-mount their storage volumes using a user-configurable encryption key. However, the cameras should only use their local storage in the event that they can not connect to the DVR. Cameras should also have tamper detection that erases the encryption key if the case is opened, or the storage card is removed. This prevents a forensic attempt to recover the encryption key, and / or gain access to the camera’s running operating system which would see the encrypted volume as a normal volume once mounted, allowing an attacker to exfiltrate the video files in cleartext.
- The DVR should require an external encryption key in order to mount the encrypted volume, in order to prevent forensic analysis. The encryption key could be unlocked by a PIN entered in to a keypad, via RFID, or NFC via your phone. The DVR should boot and run normally, even without the encryption key. However, it should block cameras from connecting, yet allow normal user administration, other than viewing files from the encrypted volume (which isn’t mounted).
- The DVR should be able to back up and restore its own configuration, as well as the configuration of all connected cameras, excluding encryption keys.
- Since the DVR itself could be stolen or destroyed, there should be a means to continuously synchronize the video files to a remote drive or cloud storage. These should be encrypted prior to transmission using Open Source tools such as PGP, where the PGP key is user-configurable, but stored on the encrypted volume so that it can’t be accessed unless the volume is unlocked and mounted.
Conclusion
If you’re not careful, you could find your cameras being used against you, or in ways you didn’t authorize.
To help protect yourself, follow these recommendations:
- Limit your use of cloud storage, and make sure your provider supports “tenant key” encryption, or as Ring calls it, End to End Encryption (E2EE). Make sure encryption is enabled, and that if there is a separate option for tenant key encryption, that it’s enabled as well.
- NEVER use Biometric authentication for you phone or other devices, because the police (or a criminal) can compel you to unlock it.
- ALWAYS use encryption. Whether you have a DVR or use cloud storage, make sure your files are encrypted.
- Isolate your cameras (and other IoT devices) from your internal network. This protects from your camera system being used as an attack vector to compromise your internal network.
- Do not use internal cameras, especially if they are tied to your doorbell cam or security system. Internal cameras, if you must use them, should be completely isolated and completely under your control.
- Adjust the field of view for all of your cameras to ensure that they are not recording sensitive areas.
- If you use a dash cam or have a car with a built-in camera system, make sure you know how to enable and disable it. When you park at home, make sure that the car’s cameras can’t record any sensitive audio or video. If you are in a collision, record the entire encounter, and then swap memory cards to preserve the evidence.